XSS hacking can happen to you while browsing the same website, what is it and how to avoid it?
XSS hacking can happen to you while browsing the same website, what is it and how to avoid it?
When you hear the term cross-site scripting (XSS), you might think it's a bit complicated and technical. This is one such method, in which hackers place malicious code on the website to trap and attack the pages that users view. Let's consider an incident as a basis to understand what this process is like.
The semi worm phenomenon
This is the most famous incident of XSS that happened in 2005. It is said that 16-year-old Sami Kamkar started the attack. He now teaches ethical hacking on YouTube. You can click here to watch his video. At that time, he was using a social networking platform called MySpace. He did one such thing, which brought about a great change.
Sami wrote a script (code) and injected it into his MySpace profile. Whoever visited his profile, his profile was infected with that code. However, the person did not know the impact on the profile.
When the judge visited Sami's profile, the person unknowingly used the code to add Sami as a friend. And, the code itself knew the message that 'but most of all, Sami is my hero'. From that it spread in such a way that those who visited Sami's profile, their profiles themselves got infected. Similarly, the profile of the person who viewed another infected profile was also infected. Within 24 hours, millions of user accounts were infected.
Sami did this cable just for fun. However, due to its impact, a situation was created where the MySpace platform had to be offline. Meanwhile, Sami got into legal trouble. It revealed how a small incident turns into a terrible incident in cyberspace.
Cross Site Scripting Attack on PayPal
The payment service provider company PayPal has been used more since its inception due to its safe and reliable transactions. In 2006, a cross-site scripting vulnerability was discovered in PayPal.
With the help of this attack, the hacker could inject malicious code into PayPal's website. Through which they forced customers to reveal their sensitive information such as credit card numbers, social security numbers and ATM PINs.
The attacker could redirect the user to a fake webpage through PayPal's genuine webpage. It is also called fishing technique (the work of ensnaring users on the Internet like baiting a fish).
In that they used to request user for login. And, the user used to submit his personal details. The attackers collected such information in large quantities. Due to this, the possibility of identity theft and financial loss of the victim users increased.
But PayPal immediately discovered and resolved this security flaw. However, this incident highlighted the importance of strong security measures to protect user data in online payment systems.
British Airways data breach
Even a big company like British Airways could not survive an attack like XSS. In 2018, the data of millions of users was exposed due to XSS vulnerability in it. Due to a vulnerability in its website, hackers managed to inject malicious code.
Due to this, the user's information, including their payment details, fell into the hands of hackers. It is said that the personal and financial information of about 380,000 customers was stolen in this way.
What is Cross Site Scripting i.e. XSS?
Before discussing this topic, let's first know how a website is made. Generally, a website is made up of three elements: HTML, CSS and JavaScript. HTML gives shape, CSS determines design and JavaScript acts like a brain. If someone can somehow control the brain, then he can do whatever he wants.
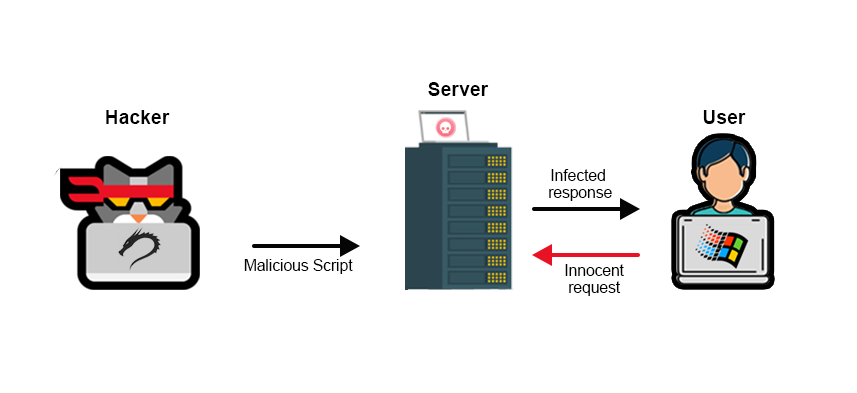
Yes, if someone knows the secret code that controls this JavaScript, they can use the website as they want. Cross-site scripting is a method used to control the website. The hacker sends such a code, so that the website goes under the hacker's control. Or let's say he does what he wants.
Now let's understand how it works. First of all, after finding the XSS vulnerability, the attacker places the malicious code in the place where the visitors are visiting frequently. When a user visits that page, then the malicious code is executed in their browser ie search. And, the script steals sensitive information such as cookies, session tokens and personal information.
There are generally three types of XSS.
1) Stored XSS
A script that is permanently placed on a targeted server such as a database or message board. It is considered to be the worst form of XSS. As it is kept forever on the target server, whenever that page is visited by a new visitor, the code is executed. That is, whatever data the code has to steal, it takes that data.
For example, Facebook has a website where we comment on various posts. Now suppose the attacker injects a script into the comment section. Since the comments are stored in the database of the Facebook website, when a person views the comment section, the attacker's code is executed in his browser. and, cookies, Besides stealing logs, activity, it leads users to malicious websites.
2) Reflected XSS
A script that displays search results or error messages to the web server. It is not stored on the server like the stored XSS above. It is called reflected XSS because it is visible on the webpage.
The attacker places a malicious link containing a script where the user clicks on it. The script is specially placed in the search bar. Then an error-like popup appears in the search bar. And, the malicious script is executed and does its job of stealing data.
For example, you visited an e-commerce site. Now search for a product in the search bar. However, a link with an error message if an attacker has injected malicious code into it
(http://example.com/search?q=<script>alert('Hacked!')</script>) shows.
In this case, if you click on the link, the code will be executed and a popup alert will appear saying that it has been hacked. Then, with the help of that code, the attacker steals your sensitive information.
3) DOM Based XSS
Such an attack, which is executed from the client side. It does not require a request with the server. For example, there is a website, which uses JavaScript to read the parameters of the URL.
And, accordingly, the content of the webpage is updated. If there is a problem with JavaScript not sanitizing the input, the attacker creates a URL like this: http://example.com/#<script>alert('Hacked!')</script>. If the website trusts the attacker's input and updates the DOM without validating, the code is executed in the user's browser and the attacker steals the data.
How to avoid?
Looking at XSS, one might think that it is a technical flaw that is only a concern of developers. However, it affects all of us. When we log in to a website, send a message or comment, we trust that the platform is secure.
However, if a hacker discovers the weakness of that website and injects harmful code into it, then our data is also stolen. Therefore, website operators should take such matters seriously. The user should not login to the same website.



Comments
Post a Comment
If you have any doubts. Please let me know.